
Written by Fran Howarth (Bloor Senior Software Analyst)
Fran's a Bloor Senior Software Analyst specialising in the field of security. For more than 20 years, Fran has worked in an advisory capacity as an analyst, consultant and writer for a number of publications, including Silicon, Computer Weekly, Computer Reseller News, IT-Analysis and Computing Magazine. More about Bloor...
Security risks are everywhere in today’s always-on, online world and everyone faces threats, from individuals, through small and medium organisations, to large enterprises. Everyone should consider themselves a target and the consequences of being hit can be dire.
Cyber security has become too important to be left to chance. Security threats are increasing in volume, severity and complexity. Attackers use increasingly advanced methods to try to breach defences – and are successful in so many cases that it is not a case of if you will be breached, but when and how often. For any organisation, a strategy focused merely on preventing attacks from reaching the network is insufficient. To safeguard sensitive data and perhaps even the business itself, the focus must shift to detection and response.
A new mindset is required for security. Security risks need to be seen in the context of overall risk, including financial and operational. Security needs to be pervasive, throughout all levels of the organisation and across all systems on and connected to the network. Only then can an organisation achieve the level of security that is required.
This paper takes a look at the stages involved in the security maturity journey and defines five stages along that journey. It then sets out to describe how organisations can move from being security blind to reaching a level of true resilience. Whilst not every organisation has the same level of risk tolerance nor unlimited budgets, organisations should consider how they can move up the scale to reach the level of security maturity that is most appropriate for them.
Cyber risks are seen as one of the greatest challenges facing developed economies today and are vastly increasing the challenges that organisations face in containing overall risk. Every organisation should consider itself a target.
According to the PwC Information security breaches survey 2015, 90% of large organisations in the UK experienced a security breach in the past year, up from 81% the previous year, and 74% of small organisations, up from 60%. Almost every organisation has sensitive data that it needs to protect, from customer and financial records, to intellectual property and trade secrets. Information such as that has great value – both to the organisation and to an ever-growing roster of criminals looking to steal it for their own gain or to compromise the organisation for ideological purposes.
Therefore, every organisation should consider itself a target and should ensure that they are doing as much as they can to adequately protect themselves. It is not a case of if an organisation has been breached, nor when; but rather how often.
As Figure 1 shows, not only are attacks becoming more frequent, but they are also increasing in severity. Slightly more than a half agree that it is extremely important to take the offensive against criminals and almost as many believe that they are vigilant in monitoring cyber attacks. However, only just over a quarter state that their budget for mitigating cyber intrusions is sufficient.

As Figure 2 shows, protecting customer information is the top driver for information security investments by a large margin, and this is something that remains consistent with earlier surveys. The need to protect the organisation’s reputation has jumped in 2014 into second place, cited by 21%, which is considerably higher than the 14% recorded in 2013, when it was placed fourth. Regulatory compliance is being seen as less of a driver, although this will likely change when the new EU data protection regulation comes into effect, with vastly increased sanctions for data breaches. Protecting intellectual property is important, but varies by industry, with the technology, consulting and professional services sectors seeing this as particularly important.
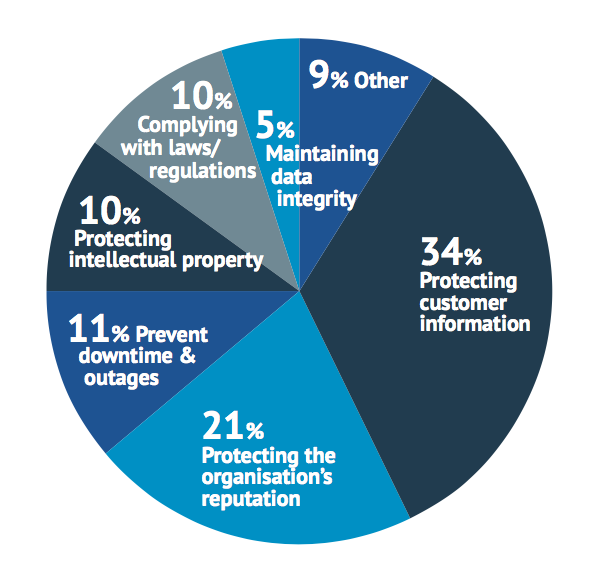
Perhaps the lack of focus on intellectual property loss is surprising in the data in Figure 2 given that respondents to the Ponemon survey depicted in Figure 3 state that it is the most damaging consequence of a cyber attack or intrusion. Should such information fall into the hands of a competitor, an organisation can see its competitive advantage dissolve.

However, the two surveys appear to agree that damage to brand and reputation can have dire consequences. In the aftermath of many of the highly publicised mega breaches that have been seen over the past couple of years, the share prices of many of the affected organisations tumbled and customers fled to competitors. According to the Risk Management Society, as much as 75% of an organisation’s value is based on its reputation.
Cisco states that 54% of organisations responding to its security capabilities benchmark study have had to manage public scrutiny of a security breach. In terms of reputational damage caused by the worst security incident of the year, PwC recently found that 17% suffered extensive adverse media coverage over a prolonged period, 17% had some adverse media coverage, and 22% received no media coverage, but had complaints from some customers.
Figure 4 looks at the fallout from the most serious security incident that organisations have suffered in the past year. Whilst smaller breaches may be easier to contain and will not necessarily be made public, more serious incidents weigh heavily on an organisation’s reputation. Add to that the loss of assets and the cost to fix the problem, and it is clear just how much a serious breach can cost an organisation.

Security breaches are increasing in volume and new technologies such as cloud computing, social networks and increasingly powerful mobile devices are making networks ever more porous, creating more chances for attackers to infiltrate organisations. Traditional security technologies and strategies are no longer up to the task of safeguarding networks.
Historically, many security technology investments have focused primarily on preventing attacks, but advanced attacks are increasingly difficult to defend against and attacks are getting through. The focus needs to change to one of incident detection and response. However, detecting incidents that have occurred is something that many organisations struggle with. And this is made harder by the tactics deployed by attackers, who look to gain a foothold on the network and then maintain a long-term presence undetected. The longer an attacker is inside the network, the greater the damage they can cause in terms of the data they are able to collect, increasing the overall cost of the breach.
In order to protect sensitive information and perhaps even to keep the business afloat, organisations need to strive to achieve a higher level of security maturity. Figure 5 depicts five levels of security maturity.
At the most basic level, organisations will be putting out fires, trying to ward off attacks with insufficient security controls, generally placed at the perimeters of the network to prevent what attacks they can from getting through. Security is seen primarily as an IT problem. But the point of IT is to increase efficiencies and keep the business running smoothly. This often leaves security under-funded.
In recent years, regulatory mandates and the need to comply with industry standards that demand security controls be placed around sensitive data have led to the need for greater investments to be made in security. Yet, this often leads to organisations investing in just those technologies that they need to achieve compliance, with little overall oversight.
As organisations move up the security maturity stack, they move from a strategy based around prevention alone to one of detection and rudimentary incident response, implementing more proactive controls and putting in place more formal policies and processes. At this stage, security becomes more integrated into the overall business and achieves more autonomy from IT.
By the time they reach the fourth level, organisations are becoming more resilient. To achieve this level, executive support is essential to drive investments in technologies that enable them to see and respond quickly to threats, backed up by a team of dedicated security personnel. They will be better able to counter even advanced threats and respond to incidents in a timely manner using countermeasures that have been developed.
The panacea is the fifth level, where a high level of security maturity has been achieved and the organisation is capable of defending against and withstanding even the most extreme attacks. Generally, the CISO has a place on the board, reporting directly to the CEO so that cyber security risks are considered alongside all the other risks that the organisation faces and a culture of security is driven throughout the business. At this point, the organisation can consider itself to be highly resilient.
In the modern economy, every company runs on IT. That makes security the business of every person in the organisation, from the chief executive to the newest hire, and not just personnel with “security” in their title or job description. Everyone should be accountable and learn how not to be a victim. Source: Cisco
To get to this point, there are a number of things that organisations need to do. They need to invest in capabilities that cut right across the threat detection and response lifecycle, backed up by strong capabilities in terms of Security Intelligence. This requires that adequate budget is allocated to security and that the entire programme is overseen by an executive with sufficient clout to bridge the traditional security communications gap between security practitioners and those in charge of the purse strings. With adequate resources dedicated to it, security can come to be seen as an enabler for the business, rather than a hindrance, and a culture of security can be driven throughout the organisation.
Having executive oversight of all of the risks that an organisation faces is essential for effective, enterprise-wide risk management and for achieving a high level of security maturity. However, although the situation is improving, this is still not the case for many organisations, which can leave them stumbling around in the dark. According to PwC, 28% of the worst breaches in the past year were caused partly by senior management giving insufficient priority to security. It found recently that 14% of security managers have never briefed their board on security risks and 21% have not briefed them in the past year. Figure 5 shows promising data in that cybersecurity is at least discussed at board meetings. However, anecdotal evidence from a recent CISO forum in the UK shows that those discussions are often limited in scope.

The National Association of Corporate Directors of the US recommends that risk oversight should be a function of the full board of directors but, as Figure 6 shows, this is only the case for a quarter of organisations that PwC surveyed. For 30%, there is no engagement of board committees or members in cyber risks.
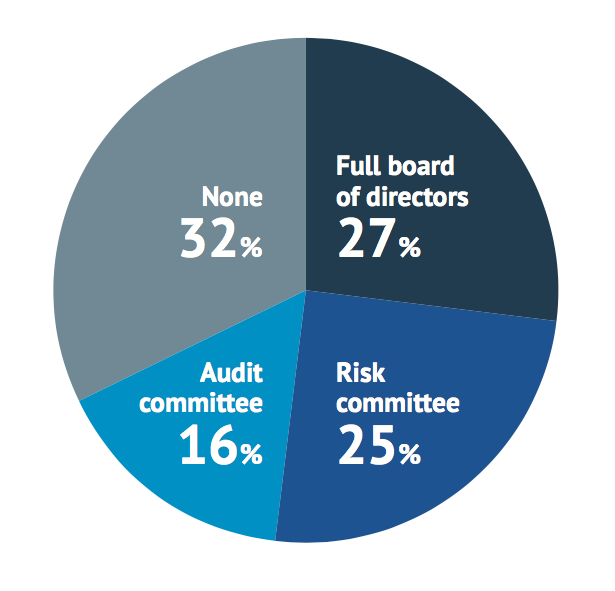
PwC believes that boards need to know about evolving risks, as well as the organisation’s security preparedness and response plans. But they can only do this if they have effective oversight of the risks faced. The text box “Why security needs board oversight” explains why board involvement is necessary.
| Why cybersecurity needs board oversight |
|---|
| The impact of cybersecurity is systemic. Incidents can impact an organisation’s global operations even when the point of risk is thousands of miles away. |
| The financial impact can be significant. |
| As regulations evolve, compliance is becoming more challenging and increasingly costly. |
| The Internet of Things has brought new threats that can cause extreme risks and tremendous physical damage. |
| >Cybersecurity insurance should be considered as a regulatory hedge against cyber risks. |
| Adversaries are working together to attack organisations. |
| Cyberattacks can result in substantial financial losses and damage brand reputations. |
The National Association of Corporate Directors recommends that risk oversight be a function of the full board, not just one committee, in order to have responsibility for cybersecurity risk. Risk must be seen as an enterprise-wide issue, not just one that concerns IT. The board needs to be in a position to be able not only to identify risks that the business faces, but to be able to determine which to avoid, accept, mitigate or transfer through insurance. ISACA states that the potential risks to consider include the proliferation of BYOD and smart devices, cloud computing, outsourcing of critical business processes to a third party, including the lack of controls around third-party services, disaster recovery and business continuity, periodic access reviews, log reviews and advanced persistent threats.
PwC warns that regulators and a plaintiff’s counsel may view the lack of substantive board consideration of operational cyber risks as meaning it does not have the required security controls in place. Preventive and detective controls that must be implemented by management, but the board is responsible for monitoring them. A board oversight programme can demonstrate that reasonable security protocols and procedures are in place. Board oversight of security is one of the key ways of moving up the security maturity scale. It will ensure that cybersecurity risks are placed on a par with all the other risks the organisation faces.
| Five principles for enhancing the oversight of cyber-risks |
|---|
| Directors need to understand and approach cybersecurity as an enterprise-wide risk management issue, not just an IT issue. |
| Directors should understand the legal implications of cyber risks as they relate to their company’s specific circumstances. |
| Boards should have adequate access to cybersecurity expertise, and discussions about cyber-risk management should be given regular and adequate time on the board meeting agenda. |
| Directors should set the expectation that management will establish an enterprise-wide risk management framework with adequate staffing and budget. |
| Board management discussion of cyber risk should include identification of which risks to avoid, accept, mitigate or transfer through insurance, as well as specific plans associated with each approach. |
The shift from prevention to detection and response requires greater Security Intelligence. According to LogRhythm, Security Intelligence is the single largest enabler of collapsing the incident response cycle via:
Security Intelligence starts with the ability to capture forensic data from every system throughout the network, whether that be an endpoint, a network security device, or even a physical security device. Every threat or incident leaves forensic traces that can be collected from log and machine-generated data from all these systems. Security Intelligence provides the ability to correlate, visualise and analyse this data, even across massive “big data” sets, to discover the sequence of how an attack occurred, how far it has spread and which systems have been impacted. By leveraging a Unified Security Intelligence Platform, context is applied to raw data from disparate sources, turning it into actionable intelligence.
According to the CyberEdge Group, security analytics technology with full-packet capture capabilities is currently the top-rated technology acquisition being planned by organisations. As Figure 7 shows, security analytics, network behaviour analysis and SIEM are all near the top in terms of planned acquisitions, all of which will help boost levels of Security Intelligence.
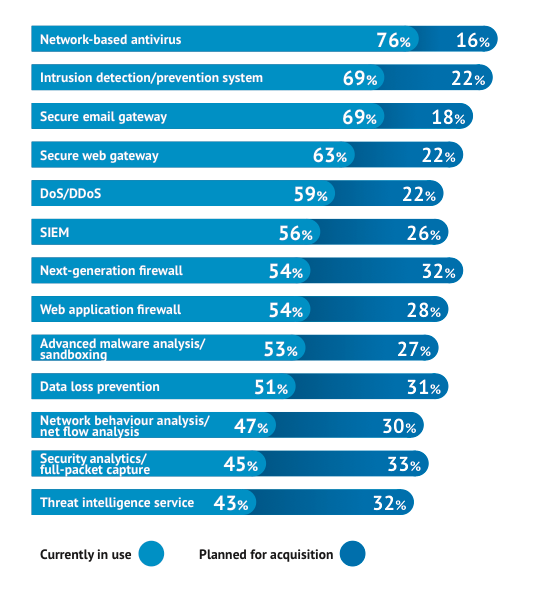
Big data analytical capabilities are essential for analysing extremely large data sets. According to the SANS Institute, respondents to its analytics and intelligence survey in 2013 did not believe that big data would stick, whereas the results of its 2014 survey indicate that the majority believe big data to be a valid approach. However, that validity is dependent on integration of analytics solutions with numerous internal detection platforms to increase visibility and improve Security Intelligence.
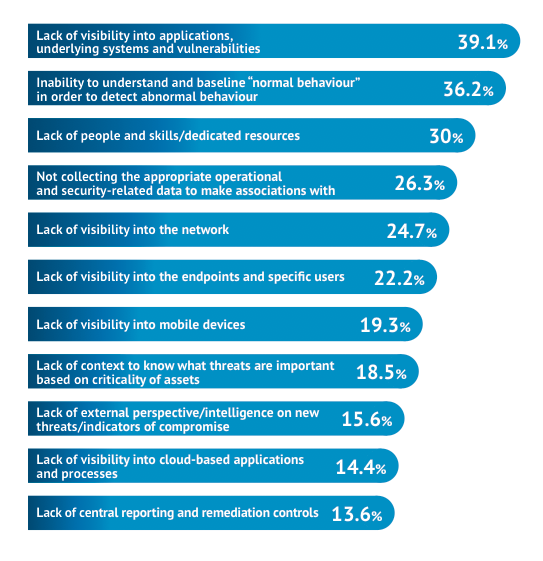
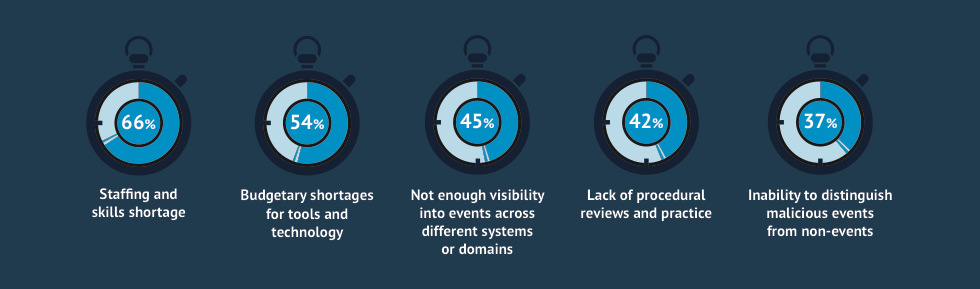
The use of a Unified Security Intelligence Platform will iron out many of the commonly cited impediments to attack detection and response, which are shown in Figure 8. One commonality among many of the responses is the lack of visibility that impedes the process of detecting and responding to incidents. Security Intelligence provide that visibility, adding context to raw data and providing the actionable insight that is required for better decision making.

The survey found that next-generation SIEM systems that can analyse and provide intelligence alerts are used by 37% and 32% use retrospective review of logs or SIEM-related data for initial discovery of security events. These technologies provide the visibility across systems from which Security Intelligence can be derived.
By leveraging machine analytics, a Unified Security Intelligence Platform provides the means to analyse all this data, enabling the organisation to be better able to assess the severity of the threat to determine whether or not further investigation is required, based on the level of calculated risk. It will find it easier to determine the root of an incident, assess its scope and determine what action to take. These are considered to be the most time consuming incident detection and response tasks.
Security Intelligence will provide organisations with the actionable insight that they need to determine the best way to respond to and recover from any security incident that occurs. This will help to quickly decide on countermeasures in order to limit the damage caused and to allow normal business operations to be resumed as quickly as possible. However, for incident response to be effective, it must be as automated as possible – especially since the top impediment to incident response is lack of dedicated in-house personnel, as shown in Figure 10.
Once the Security Intelligence Platform has identified a threat and determined that it poses a real risk, organisations should move on to the investigation stage. At this point, the threat will be fully analysed to determine its scope and level of risk so that countermeasures can be decided on that can mitigate the risk posed. Any technology chosen should provide a suggested range of countermeasures to be taken. Where the risk of using the chosen countermeasure is deemed to be low and there is little likelihood of further disruption, such as a critical system being taken offline, fully automated remediation can take place. Where the risk of implementing a fully automated response is perceived to be higher, human guidance steps should be included whereby security personnel and managers review the remediation process prior to implementation and assess the results during and after the process.
As organisations move beyond firefighting and compliance-oriented mindsets and switch from a policy of prevention alone to threat detection and response, Security Intelligence is vital for guiding organisations through the process. It will add context to raw data collected from throughout the network, giving organisations the intelligence and actionable insight that they need for more informed decision making. It will help guide organisations along the path to achieving full security maturity.
However, all parts of the business and every system on or connected to the network must be included if full security maturity can be achieved. To achieve pervasive security, everyone must be involved in the organisation, from top-level executives to the newest hires. Security requires board-level sponsorship and oversight so that it given the priority that is required so that even the most complex and pervasive threats can be countered.
All organisations are at risk of a security breach that could have extremely damaging consequences. Taking into account their own appetite for risk and any budgetary constraints, every organisation should strive to achieve as resilient a security posture as possible.
Security Intelligence provides the visibility that is necessary for being able to not just detect, but to respond to threats and vulnerabilities on the network and all endpoints that are connected to it by providing the relevant information and context that provide the actionable insight needed for effective decision making. With such capabilities, organisations will be able to move up the security resilience scale to the point where they have the confidence that they are doing the most that they can for protecting sensitive assets and safeguarding the organisation.

This spotlight report was brought to you in partnership with the software analyst firm Bloor. Click here for more information on Bloor, here for more content from Crozdesk and here to start a software search.